FIDO credentials help CISOs build trust, prevent credential theft and support FFIEC compliance mandates.
Credential theft is the new digital bank heist — and CISOs know the stakes: stolen funds, regulatory fines and eroded customer trust. For financial institutions navigating FFIEC and similar frameworks, preventing credential theft isn’t optional — it’s mission-critical.
Attackers don’t always target customers; increasingly, they target employees. Through phishing scams, compromised devices or credential reuse, bad actors gain access to internal systems — opening the door to ransomware, data exfiltration and reputational harm.
It’s a popular heist, and an expensive one. In fact, more than two-thirds of security breaches involve stolen or compromised credentials — and the consequences can be devastating. In late 2025, a major UK institution, Co-op, was forced offline after a cyberattack disrupted its operations and exposed sensitive data. They reported a loss of at least £206 million in revenues, underscoring how credential-based attacks can cripple critical services and damage public trust. Beyond direct losses, organizations face operational disruption, reputational damage and escalating recovery costs when employee credentials are compromised.
And in spite of the industry’s efforts to inform people about the danger, credential theft remains startlingly common. In mid-2025, security researchers reported 16 billion stolen credentials, including log-ins tied to Apple, Google, Facebook and corporate systems. A few months later, both Google and Microsoft issued additional warnings about the growing prevalence of credential theft.
No wonder two-thirds of CISOs say they’re concerned about the security of their identity management solutions. Though many scammers target consumers, employees are just as vulnerable to compromised credentials and passwords — leaving organizations exposed to dangerous attacks and the costs associated with them.
In this article, we’ll explain how passwordless authentication solutions and, in particular, device-bound passkeys such as smart cards and security keys, are rising to meet these challenges. The FIDO Alliance has charted the traction that passkeys have gained in the workforce. Device-bound passkeys are especially well-suited to the financial services industry because of the high level of trust they offer — trust that’s relevant to regulators as it is to employees.
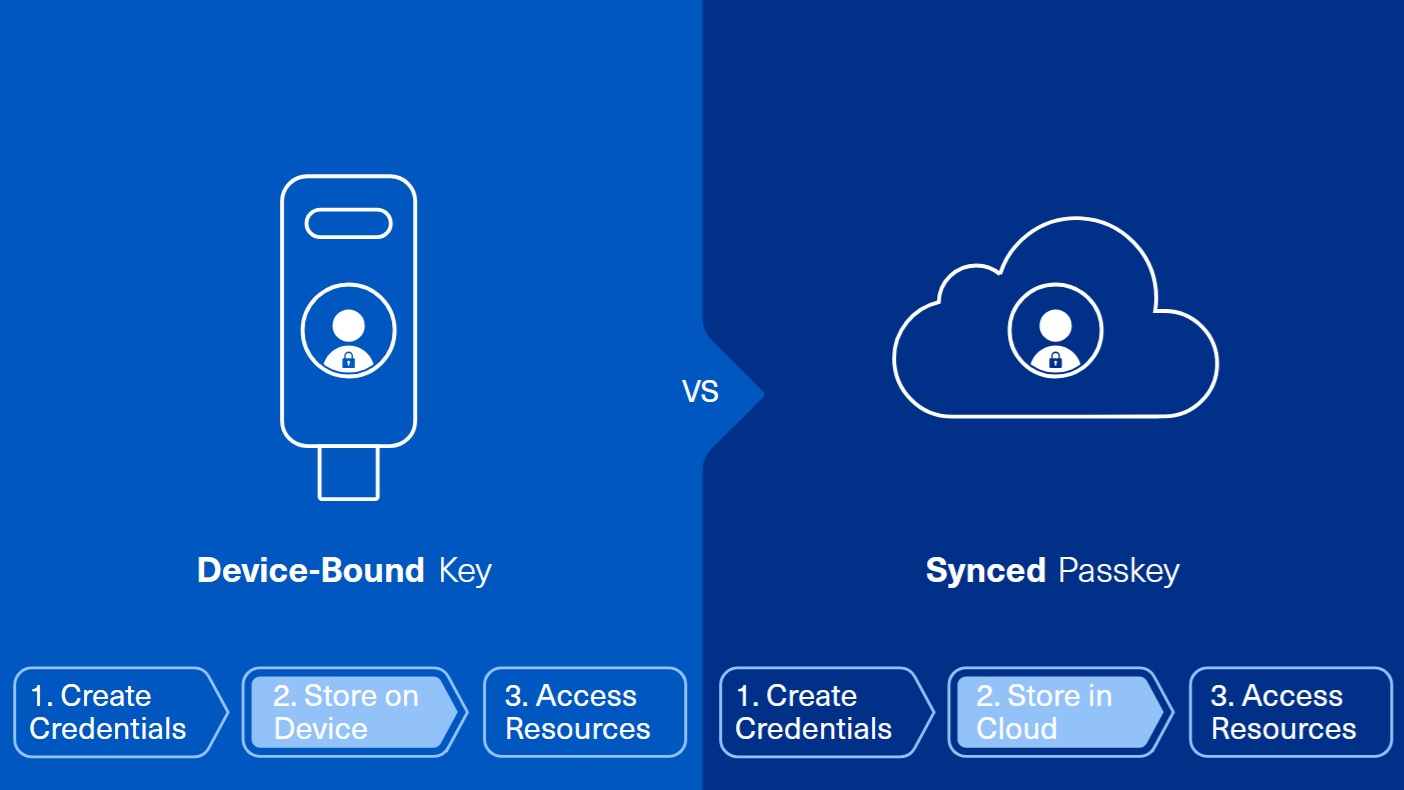
What Are Device-Bound Passkeys?
- Synced passkeys are stored in the cloud and can be accessed across multiple devices
- Device-bound passkeys, sometimes known as hardware-based passkeys, are stored on a device like a USB key or card — and can only be accessed on that device
Device-bound passkeys enhance security by tying authentication to a specific, trusted device. Synced passkeys — while backed by secure hardware and end-to-end encryption — introduce a broader attack surface because they rely on cloud synchronization and multi-device access, not because attackers can directly access keys in the cloud. Device-bound passkeys, by contrast, are useless to attackers who harvest leaked credentials. Because they must possess a physical device to use their private key, fraudsters cannot access the credentials to execute remote attacks.
Top 4 Benefits of Device-Bound Passkeys for Financial Institutions
Device-bound passkeys give employees a fast, easy way to authenticate their identities. Built on FIDO-based authentication, they also enable financial service institutions to:
- Prevent Credential Theft — They are phishing-resistant and difficult to compromise or steal, preventing costs and reputational damage related to data breaches
- Support FFIEC — HID’s device-bound FIDO credentials help financial institutions meet evolving authentication requirements for employees and third parties. They provide audit trails for regulators and align with FFEIC identity security standards.
- Deepen Trust — Financial institutions can use device-bound passkeys to offer a seamless authentication experience to their employees without sacrificing protection
- Lower Operational Expenses — Replacing passwords with passkeys helps institutions significantly reduce help desk calls and improve productivity. According to the FIDO Alliance, organizations that deploy passkeys experience 81% fewer login issues, 73% faster access and 77% fewer help desk calls.
How to Implement — and Scale — Device-Bound Passkeys
Scalability is one of the most common concerns that CISOs have about implementing FIDO credentials. HID — which supports device-bound passkeys with compliance-aligned smart cards and hardware tokens that anchor passkeys to trusted devices — helps institutions tackle each of these with a phased approach that includes:
- Migration Planning — Passkeys don’t have to be deployed all at once. Instead, they can be rolled out in a series of manageable, step-by-step phases, starting with a modest pilot, then expanding and operationalizing over time. The first step is finding solutions that increase security now while building momentum for the future — like using existing ID badges or smartphones as FIDO credentials. Successful deployments typically begin by prioritizing specific groups like technically proficient users or high-risk roles before expanding new use cases. Here’s our Passkey Playbook to learn more about deploying passkeys effectively across your enterprise.
- User Education — Drive adoption with targeted internal communications, enrollment support and helpdesk enablement. Then, keep track of helpdesk trends and feedback to identify areas that need to be tweaked or improved.
- Device Lifecycle Management — Rolling out passkeys isn’t just about issuing secure credentials — it’s about managing them with the same precision as the rest of your identity stack. With HID’s enterprise passkey management solution, organizations have the tools they need to provision FIDO credentials at scale and support compliance mandates with provisioning, resetting and management capabilities. Request a demo of our Enterprise Passkey Management solution to learn more about managing FIDO credentials at scale.
View the passkey implementation infographic >>
Device-Bound Passkeys and Regulatory Compliance
Mandates and regulations like FFIEC are ever evolving. One thing that financial institutions can expect to see in future iterations? Ever-stricter requirements around authentication and fraud prevention. Adopting passkeys helps CISOs stay ahead of new mandates while meeting current guidelines like:
- FFEIC — The Federal Financial Institutions Examination Council (FFIEC) expanded authentication requirements to cover not just customers, but employees and third parties who access services and systems. Device-bound passkeys set banks up for compliance by anchoring each user’s identity to a trusted device — and streamlining both visibility and incident response.
- PSR — Payment service providers must ensure that employees are adequately trained to mitigate payment fraud risks — including the risk that they will themselves be the targets of credential theft. By eliminating password-related vulnerabilities, passkeys provide critical ammunition for the fight against this type of scam.
Prevent Credential Theft, Streamline Authentication
Gone are the days when bank heists were carried out by masked criminals in the lobby. These days, they are carried out more quietly using leaked credentials. Device-bound passkeys are the unpickable lock that stops that threat and prevents credential theft — without slowing down customer transactions.
Request your free sample now and explore the power of device-bound passkeys >>
Frequently Asked Questions
1. What are device-bound passkeys?
Device-bound passkeys — also known as device-bound FIDO credentials — are cryptographic credentials that are stored locally on a device like a mobile phone or smart card. Because they are never synced to the cloud, they are phishing resistant.
2. What is the difference between synced and device-bound passkeys?
Synced passkeys can be used across multiple devices, but they are always protected: the cloud only stores an encrypted copy, and the keys to decrypt it stay on the user’s devices. Device-bound passkeys are tied to a single trusted device, making them naturally resistant to remote attacks.
3. Why are device-bound passkeys important for CISOs in financial institutions?
They eliminate password-related vulnerabilities, reduce phishing risk and help meet compliance mandates like FFIEC — all critical for fraud prevention strategies.
4. How do device-bound passkeys prevent credential theft?
Passkeys consist of one key pair, one private, and one public key. The private key never leaves the device to which they were issued — making it extremely difficult for the credentials to be stolen.
5. Do device-bound passkeys support FFIEC compliance?
Yes. Device-bound passkeys offer clear audit trails and strong authentication for financial institutions aligned with FFIEC and NIST standards.
6. What are the benefits of device-bound passkeys for banks?
Passkeys support credential theft prevention initiatives while protecting access to core banking systems, workstations and applications. They also improve productivity, support compliance mandates and lower helpdesk costs.
7. How can financial institutions implement device-bound passkeys?
HID recommends a phased approach to passkeys that includes pilot programs, device life cycle management and user education to ensure successful rollout.
8. How do device-bound passkeys align with FIDO standards?
HID’s passkeys follow FIDO authentication protocols, ensuring interoperability and strong cryptographic security.
9. What are the scalability options for large enterprises?
HID recommends a phased rollout starting with high-risk roles, supported by life cycle management tools and internal education campaigns. Learn more in our Passkey Playbook.
10. Are device-bound
Yes. Device-bound passkeys offer strong resilience against AI-driven phishing and automated attacks because they rely on domain-bound cryptographic keys and require user interaction (such as biometric or PIN), which AI cannot replicate. While no method is immune to every future threat, passkeys align with zero-trust principles and position institutions well for evolving AI-enabled security and regulatory landscapes.